How Strategic Planning relates to Enterprise Architecture?
TOGAF often refers to Strategic Planning without specifying the details of what it consists of. This document explains why there is a perfect fit between the two.
Strategic Planning means different things to different people. The one constant is its reference to Business Planning which usually occurs annually in most companies. One of the activities of this exercise is the consideration of the portfolio of projects for the following financial year, also referred to as Project Portfolio Management (PPM). This activity may also be triggered when a company modifies its strategy or the priority of its current developments.
Drivers for Strategic Planning may be
· New products or services
· A need for greater Business flexibility and agility
· Merger & Acquisition
· Company’s reorganization
· Consolidation of manufacturing plants, lines of business, partners, information systems
· Cost reduction
· Risk mitigation
· Business Process Management initiatives
· Business Process Outsourcing
· Facilities outsourcing or in sourcing
· Off shoring
Strategic Planning as a process may include activities such as:
1. The definition of the mission and objectives of the enterprise
Most companies have a mission statement depicting the business vision, the purpose and value of the company and the visionary goals to address future opportunities. With that business vision, the board of the company defines the strategic (e.g. reputation, market share) and financial objectives (e.g. earnings growth, sales targets).
2. Environmental analysis
The environmental analysis may include the following activities:
· Internal analysis of the enterprise
· Analysis of the enterprise’s industry
· A PEST Analysis (Political, Economic, Social, and Technological factors). It is very important that an organization considers its environment before beginning the marketing process. In fact, environmental analysis should be continuous and feed all aspects of planning, identify the strengths and weaknesses, the opportunities and threats (SWOT).
3. Strategy definition
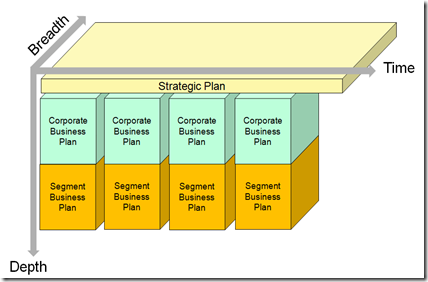
Based on the previous activities, the enterprise matches strengths to opportunities and addressing its weaknesses and external threats and elaborate a strategic plan. This plan may then be refined at different levels in the enterprise. Below is a diagram explaining the various levels of plans.
To build that strategy, an Enterprise Strategy Model may be used to represent the Enterprise situation accurately and realistically for both past and future views. This can be based on Business Motivation Modeling (BMM) which allows developing, communicating and managing a Strategic Plan. Another possibility is the use of Business Model Canvas which allows the company to develop and sketch out new or existing business models. (Refer to the work from Alexander Osterwalder http://alexosterwalder.com/).
The model’s analyses should consider important strategic variables such as customers demand expectations, pricing and elasticity, competitor behavior, emissions regulations, future input, and labor costs.
These variables are then mapped to the main important business processes (capacity, business capabilities, constraints), and economic performance to determine the best decision for each scenario. The strategic model can be based on business processes such as customer, operation or background processes. Scenarios can then are segmented and analyzed by customer, product portfolio, network redesign, long term recruiting and capacity, mergers and acquisitions to describe Segment Business Plans.
4. Strategy Implementation
The selected strategy is implemented by means of programs, projects, budgets, processes and procedures. The way in which the strategy is implemented can have a significant impact on whether it will be successful, and this is where Enterprise Architecture may have a significant role to play. Often, the people formulating the strategy are different from those implementing it. The way the strategy is communicated is a key element of the success and should be clearly explained to the different layers of management including the Enterprise Architecture team.
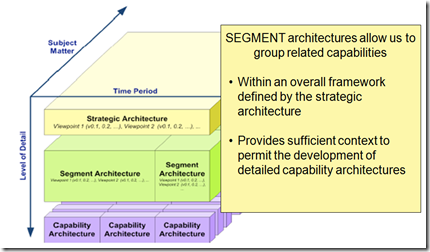
To support that strategy, different levels or architecture can be considered such as strategic, segment or capability architectures.
Figure 20-1: Summary Classification Model for Architecture Landscapes
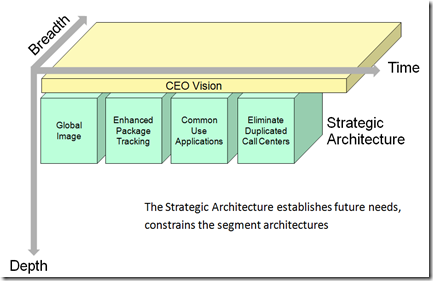
This diagram below illustrates different examples of new business capabilities linked to a Strategic Architecture.
It also illustrates how Strategic Architecture supports the enterprise’s vision and the strategic plan communicated to an Enterprise Architecture team.
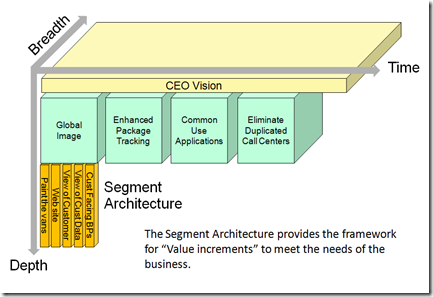
Going to the next level allows better detail the various deliverables and the associated new business capabilities. The segment architecture maps perfectly to the Segment Business Plan.
5. Evaluation and monitoring
The implementation of the strategy must be monitored and adjustments made as required.
Evaluation and monitoring consists of the following steps:
1. Definition of KPIs, measurement and metrics
2. Definition of target values for these KPIs
3. Perform measurements
4. Compare measured results to the pre-defined standard
5. Make necessary changes
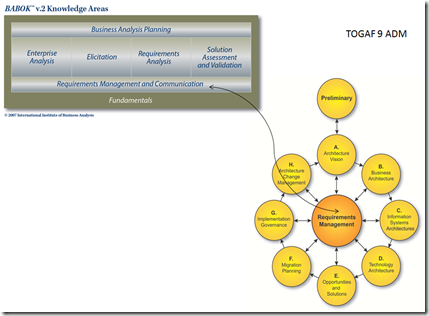
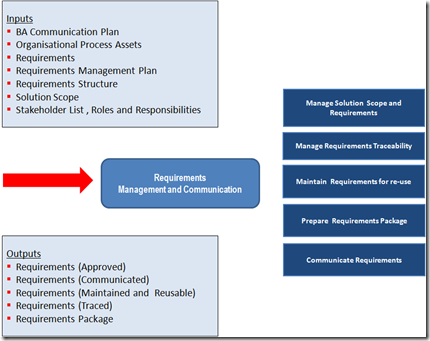
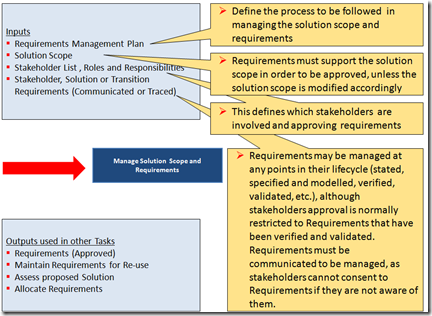
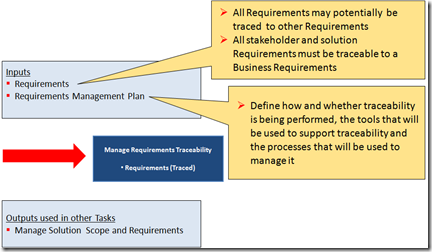
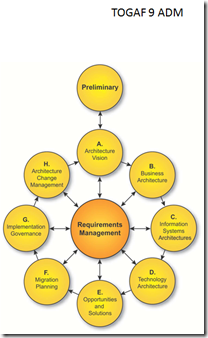
Strategic Planning and Enterprise Architecture should ensure that information systems do not operate in a vacuum. At its core, TOGAF 9 uses/supports a strong set of guidelines that were promoted in the previous version, and have surrounded them with guidance on how to adopt and apply TOGAF to the enterprise for Strategic Planning initiatives. The ADM diagram below clearly indicates the integration between the two processes.
The company’s mission and vision must be communicated to the Enterprise Architecture team which then maps Business Capabilities to the different Business Plans levels.
Many Enterprise Architecture projects are focused at low levels but should be aligned with Strategic Corporate Planning. Enterprise Architecture is a critical discipline, one Strategic Planning mechanism to structure an enterprise. TOGAF 9 is without doubt an effective framework for working with stakeholders through Strategic Planning and architecture work, especially for organizations who are actively transforming themselves.